Jamie StevensenIs it possible to achieve a single source of truth in cyber security?
Growing trend in cyber-attacks, despite the increasing number of security tools being bought.
With years of experience in looking after complex IT environments, the ThreatAware founders recognised a growing trend in cyber-attacks, despite the increasing number of security tools being bought. Appreciating the near-impossible task faced by IT teams in understanding how well different security tools were deployed across their estate, they embarked upon a mission to empower organisations in their defence against these threats. They believed that what businesses really needed was a single source of truth. But is it really possible to achieve, and why is it so important?
Security tools are clearly vital to preserving an organisation’s data accuracy and integrity but, for many organisations, monitoring these tools has led to increased workload, compliance concerns and reporting challenges. Studies show that nearly half of organisations lose up to 80 person-hours to a full security asset inventory. For this reason, most organisations only do this in full once a month or even less and so have limited data on the functionality and deployment of these tools.
Alongside this, another common challenge in cyber asset management is being able to find all your assets in the first place. Modern-day IT environments are often fragmented and agent-based methods, such as CMDB, or log ingestion methods are regularly incapable of finding every asset.
So, what happens? Often, these challenges feel insurmountable and IT teams have to accept not being able to confidently say that all security tools are working as they should on every machine accessing company data.
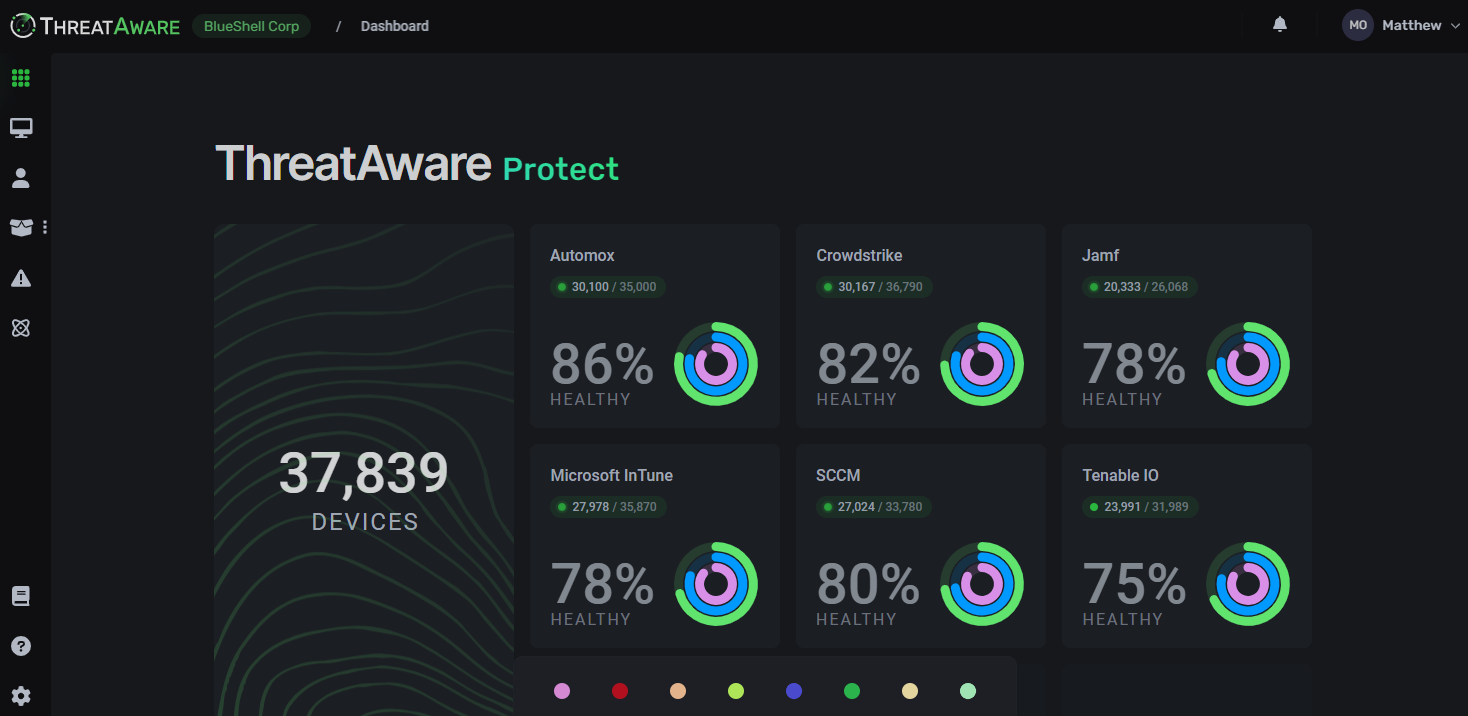
ThreatAware founders Jon Abbott and Steve Thomson came across this problem some six years ago and decided to find a solution that could give organisations a single source of truth. They felt that a system which could collect data directly from security tools and contextualise that data into a single list might be the answer to getting a highly accurate picture of an entire IT estate.
Since then, they’ve developed and evolved the ThreatAware platform to what it is today. Through a unique, patent-pending timeline matching algorithm, the platform builds upon traditional metadata matching methods to standardise data from disparate systems with remarkable accuracy – giving organisations that elusive, perfect single source of truth.
ThreatAware gives organisations instant visibility of their entire IT estate, automatically highlighting areas vulnerable to attack. Armed with this knowledge, IT teams can efficiently and proactively reduce their attack surface and be confident in their ability to prevent breaches.
If you’d like to find out more about how ThreatAware can help you achieve a single source of truth, get in touch with us or find our recent podcast here.
Ready to protect all your assets?
Leveraging its proprietary timeline-matching technology, ThreatAware ensures you have a complete, accurate, and non-duplicated asset inventory in real-time. No more guesswork – spot and fix deficiencies across your entire IT estate instantly.
Onboard in less than 30 minutes.
Request a Trial